Mobile network security offer opportunities
Updated: 2013-09-18 11:16Speed, flexibility and simplicity will become key indicators for cloud security solutions. Cloud computing ecosystem vendors and service providers are increasing their investments in cloud computing to improve the reliability, usability and data security of the cloud computing platform to ensure the healthy development of cloud computing.
"China entered the big data era in 2012. Big data analysis will transform the network security protection technologies. It is an inevitable trend that big data analysis and security technologies will integrate, and the technologies based on traditional security including virus resistance, firewall, and an intrusion prevention system will accelerate the transformation to big data analysis- and monitoring-based security technologies. This will impact China's information security technology and product research and development, as well as network security defense system construction."
The popularity of social networks provides new opportunities for online fraud. As a result, social network users and their friends, colleagues and family members are cheated by these criminals.
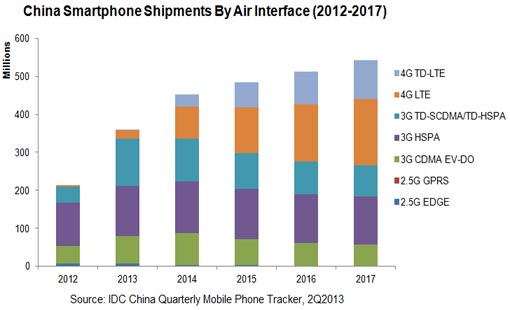
Social networks challenge enterprise security strategies. Although social networks can boost the marketing efforts of enterprises, the benefits must be balanced with information security management and the risk of information breaches. At the recent Black Hat USA 2013 conference, mobile computing became a new area for people to research. According to IDC, the total shipment of China smartphones in Q1 2013 was 79 million with a year-on-year growth of 120%, while tablets reached 6.20 million with a year-on-year growth of 163.5%, exceeding the shipment of smartphones in the first half of 2012. As market shares of desktops and laptops decrease and more people use tablets and smartphones to access to data and applications stored in the cloud platform, the system bugs are becoming more harmful. At the same time, enterprises are beginning to consider deploying BYOD solutions, which makes enterprise-level mobile security protection more complicated.
In view of these factors, IDC suggests that enterprises formulate a thorough mobile security protection strategy while deploying mobile applications, and utilize the mobile appliance and application management solutions to integrate mobility and security, thereby minimizing security risks.